Vendor due diligence is a crucial part of effective risk management. Sadly, it’s a practice that many companies overlook. Indeed, one out of three organizations report they conduct little to no vendor due diligence. So, it should be no surprise that an estimated 51 percent of companies have experienced a data breach due to third-party access. From ransomware to service interruptions, every vendor and supplier you work with has the potential to introduce risk to your organization.
Indeed, poor third-party due diligence may lead to costly consequences. Every year, we hear about lost revenue, reputational damage and legal action resulting from vendor due diligence gone wrong. No matter the size of your organization, exploring the fundamentals of effective vendor due diligence is wise.
In this blog, we’ll provide a guide to vendor due diligence. To begin, we’ll offer key definitions and basics of the practice. Next, we’ll share how often you should evaluate vendors as well as the three areas to assess. Finally, we’ll offer a due diligence checklist, examples of due diligence questionnaires (DDQs) and real-life examples of the cost of poor third-party risk management.
- Vendor due diligence basics
- What is vendor due diligence?
- When to review vendor risk
- The supplier due diligence process
- 3 factors of vendor due diligence
- Template: Vendor due diligence checklist
- Vendor due diligence examples to explore
- Sample vendor due diligence questionnaires
- Vendor risk realized: Real-life outcomes
- Vendor due diligence basics
Vendor due diligence basics
What is vendor due diligence?
Vendor due diligence is the process of evaluating the risks involved in partnering with a particular vendor or supplier. Also known as supplier due diligence, buy-side due diligence or vendor risk management, it helps organizations avoid or mitigate threats.
Likewise, vendors may also perform due diligence. This is called seller-side due diligence. Generally, it’s part of a discussion to bid or not to bid on a request for proposal (RFP) issued by a buyer.
When to review vendor risk
Sourcing new vendors
Your first vendor due diligence assessment should occur during the procurement process.
To avoid unnecessary work for your vendors, we recommend issuing a vendor risk assessment only to a shortlist of candidates. Typically, the shortlist should be a group of up to five vendors who provided the strongest proposals. Once you’ve identified this group, create and send your due diligence questionnaire. Then this should be a part of your final RFP scoring considerations.
Periodically during the partnership
Circumstances, regulations and risk factors change constantly. Accordingly, it’s important to maintain up-to-date records throughout the life of the partnership. So, make the vendor due diligence process a part of your routine supplier relationship management practices.
The frequency of these updates should vary based on the importance of the vendor to your processes. We recommend conducting vendor due diligence on a recurring basis — either quarterly, biannually or annually.
A change of circumstances
When changes happen outside of the regular evaluation cycle, you may need to request an updated DDQ. There are a few scenarios to look for:
- Mergers and acquisitions involving the vendor
- Updated or new features and enhancements
- New local, state or federal regulations
- Changes in company leadership
The supplier due diligence process
In most cases, procurement manages the vendor due diligence process as part of their ongoing supplier relationship management efforts.
- Engage vendor contacts and internal stakeholders
- Determine which internal stakeholders must be involved (IT, finance, legal)
- Provide an overview of the vendor’s services
- Define information or applications the vendor will have access to
- Determine what risk level the vendor poses to your organization
- Ask questions about compliance, security and user risks
- Send a questionnaire request to the vendor
- Follow up with the vendor to remind them to complete the questionnaire
- Review vendor responses and documentation to evaluate risk
- Determine the importance, impact and likelihood of each vendor risk
- Draft vendor action plan or determine next steps to protect your organization
- Gather and catalog vendor data for comparison to future evaluations
As you can see, there are a lot of considerations when conducting vendor due diligence. Essentially, the information technology, human resources and legal teams all independently assess each vendor.
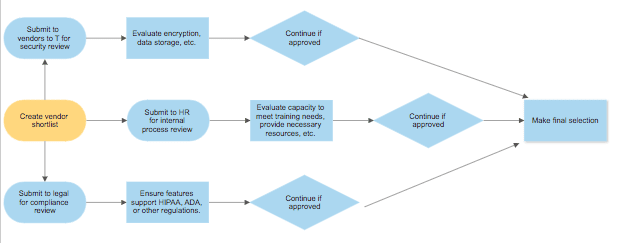
You may notice that the steps in the vendor due diligence process are similar to those in the RFP process. Consequently, RFP software centralizes and automates supplier risk assessments as well.
3 factors of vendor due diligence
1. Compliance
One of the most important aspects of vendor due diligence is verifying compliance. Many organizations need their vendors to comply with or support regulations like:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act of 1996 (HIPAA)
- Fair Labor Standards Act (FLSA)
- Americans with Disabilities Act of 1990 (ADA)
Vendor compliance is crucial. Failure to comply with regulations due to a vendor mistake, doesn’t get your organization off the hook. Indeed, you may face consequences including fines and legal fees.
Consider ADA compliance. According to the Equal Employment Opportunity Commission:
“Title I of the Americans with Disabilities Act of 1990 (the “ADA”) requires an employer to provide reasonable accommodation to qualified individuals with disabilities who are employees or applicants for employment…”
So, if you’re purchasing an applicant tracking system (ATS) with a job portal, understanding whether your vendor can support this accommodation is critical. Specifically, you would need to know how the ATS integrates with systems that assist hearing- or vision-impaired applicants.
2. Security
One of the most common vendor risks is the threat of data exposure via a third party. It seems like there’s a new data breach every week. Accordingly, assessing data security is another major element of vendor due diligence. Companies considering investing in financial software or services, in particular, must do their homework before making a purchase.
And, like with compliance, responsibility for a vendor’s security failure ultimately falls to the organization.
Security in banking and financial services
In an article on Reuters, Abel Clark, chief executive officer of TruSight and former Thomson Reuters executive, noted that the financial services industry has seen increased innovation in recent years. This has led to more companies partnering with third-party vendors, which opens them up to greater risk.
To mitigate these risks, the Office of the Comptroller of the Currency (OCC), a division of the U.S. The Department of the Treasury, offers guidance for “national banks and federal savings associations (collectively, banks) for assessing and managing risks associated with third-party relationships.”
They state that an effective vendor risk management program should include:
- Plans that outline the bank’s strategy, identify the inherent risks of the activity, and detail how the bank selects, assesses and oversees the third party
- Proper due diligence in selecting a third party
- Written contracts that outline the rights and responsibilities of all parties
- Ongoing monitoring of the third party’s activities and performance
- Contingency plans for terminating the relationship in an effective manner
- Clear roles and responsibilities for overseeing and managing the relationship and risk management process
- Documentation and reporting that facilitates oversight, accountability, monitoring and risk management
- Independent reviews that confirm the bank’s process effectively manages risks
Of course, banks aren’t the only organizations that need to mitigate risk through vendor due diligence.
Software security assessments
Mary Ann Davidson, chief security officer at Oracle, recommends asking software vendors the following questions as part of your risk assessment process, regardless of industry.
Recommended risk assessment questions for software vendors
- Do you have a formal development process that includes security?
- Are developers trained on secure coding?
- Is compensation tied to secure coding practices?
- Are products assessed by security experts (in-house or other)?
In addition, you may also wish to consider factors such as encryption capabilities and data center tiers.
3. User risks
“Human error is a major factor in breaches, and trusted but unwitting insiders are to blame. From misaddressed emails to stolen devices to confidential data sent to insecure home systems, mistakes can be very costly.” – Harvard Business Review
Vendor due diligence should always consider how vendors protect you from internal risk.
For example, many electronic health records (EHR) systems now offer mobile capabilities. This allows doctors and nurses to document patient information from their phone or tablet. Indeed, while this technology often increases adoption of the EHR and allows medical professionals to hold more engaging conversations with patients while updating records in real time, it opens organizations to risk.
If a doctor or nurse loses their phone or tablet, it could easily fall into the wrong hands. Consequently, an unauthorized person could then gain access to patient records, violating their rights under HIPAA.
With the right capabilities, however, vendors can help mitigate or even prevent this problem. Multi-layered user authentication can prevent unauthorized records access, for instance. In addition, the EHR vendor might even provide a way to remotely delete patient information from a device.
When evaluating software or any organization that will manage your data, make sure to identify areas where users can unintentionally introduce risk. Then, determine whether your vendor can help close these security gaps.
Template: Vendor due diligence checklist
Between compliance, security and protecting against potential user risks, completing vendor due diligence can certainly seem a bit overwhelming.
To help simplify the process, we put together this 16-point vendor due diligence checklist. Use it as a starting point to evaluate potential risk.
- Does the vendor offer flexible user permissions?
- Can you delete data from stolen mobile devices?
- Is multi-level user authentication required?
- Will the vendor provide training for your staff?
- How does the vendor train their own staff?
- Will you receive alerts about suspicious activity?
- Does the contract adequately detail ownership and responsibilities?
- Is data stored in multiple, redundant servers?
- Are the data centers adequately tiered?
- Does the vendor offer 192- or 256-bit encryption?
- Do they offer version tracking?
- Will you have access to downtime tracking and updates?
- Is there adequate database auditing?
- Does the vendor have a documented security strategy?
- Are documented contingency plans in place?
- Do independent agencies conduct security reviews?
Vendor due diligence examples to explore
One of the simplest ways to engage in vendor due diligence is with a due diligence questionnaire. However, DDQs must be very thorough to properly assess and mitigate vendor risk.
Starting from an example is always helpful to ensure you don’t miss anything crucial.
Sample vendor due diligence questionnaires
- Anti-bribery compliance DDQ example – MISC
- Vendor due diligence policy – JLL
- Supplier due diligence guide – Fidelity investments
- Vendor due diligence questionnaire – FIA
For more real-world DDQ examples, check out this blog: 9 of the best DDQ examples. There you can see how organizations are using DDQs to uncover hidden risks and financial pitfalls — before making a purchase.
Vendor risk realized: Real-life outcomes
Target data breach
In 2013, Target confirmed a security breach. Hackers gained access to customer data — including names, credit card information, and more. According to Shirley Inscoe, fraud expert and AITE analyst, “This incident appears to be tied to their [point-of-sale] system.”
As a result, Target agreed to pay $18.5 million to 47 states and the district of Columbia. That’s in addition to the $202 million they spent on legal fees and other costs related to the breach.
Volvo seat belt recall
For years, Volvo built their brand around a reputation for safety. Unfortunately, in 2021 the company faced a recall of around 19,000 vehicles due to faulty passenger seat belts. The incident impacted cars with seat belts provided by a specific third-party vendor. The total expense of the recall wasn’t disclosed. However, the damage to Volvo’s image was probably more costly.
Morgan Stanley data breach
In 2016, finance giant Morgan Stanley hired a vendor to handle the shut down of two legacy wealth management data centers. Unfortunately, the company didn’t conduct sufficient vendor due diligence when selecting the service provider contracted to perform the work. Furthermore, Morgan Stanley neglected to conduct regular reviews of the vendor’s performance as time went on.
Eventually, hackers took advantage of the third-party vulnerability in two separate data breaches. The hackers illegally accessed information from more than 15 million customers. Indeed, the lost data included names, addresses, social security numbers, dates of birth and stock plan details. As a result, Morgan Stanley faced a class action suit that settled for $60 million.
Conclusion
Ultimately, partnering with the right vendor is more complex than simply comparing prices. The right vendor should protect you from risk. Admittedly, performing effective vendor due diligence takes time and effort. But, it’s well worth it.
Originally published May 23, 2019 — Updated January 19, 2022
